Tech_Supp0rt


A box of how a scammer’s server got hacked due to some unpatched vulnerabilities.
Nmap scan — identifies the open ports:
22/tcp — ssh(secure shell)
80/tcp — HTTP
139/tcp — Netbios-ssn
445/tcp — SMB(samba share)

SSH seems like a dead end because we lack credentials to access the system. Enumerating port 80 –HTTP displays a default apache web page where we can conclude the OS running is Linux OS

Performing a directory brute force using dirsearch found in https://github.com/maurosoria/dirsearch there were only 2 subdomains;
- Wordpress
- Test

Further enumerating wordpress using wpscan to obtain a potential vulnerability seemed like a dead end Enumerating SMB I was able to login with no password and discovered a file called enter.txt which I was able to download and view its contents.

The content of enter.txt contains instructions and a username:admin & credentials.

One thing takes my attention, the subrion site

Navigating to the subrion site seems like a dead end but after intercepting with burpsuite and sending the request to the repeater with the path subrion/robots.txt, a path subrion/panel/ discovers a login page which after attempting the credentials under enter.txt we are able to login to the system.


During the enumeration process ,Wappalyzer reveals that the site is running Subrion as a CMS and I also discovered a file upload function in the system.

Setting out to look for a specific CVE for the subrion CMS using searchsploit I discovered a file upload vulnerability.

Download the code and edit changing the IP and paths

Exploiting the CMS gives us a connection a web shell…Hurray!!!!!! We need more than just a web shell!!!!

After enumerating the system I was able to discover that the system accepts .phar extension upload
Navigated pentest monkey on Github where I was able to download and upload a php reverse shell on the system.
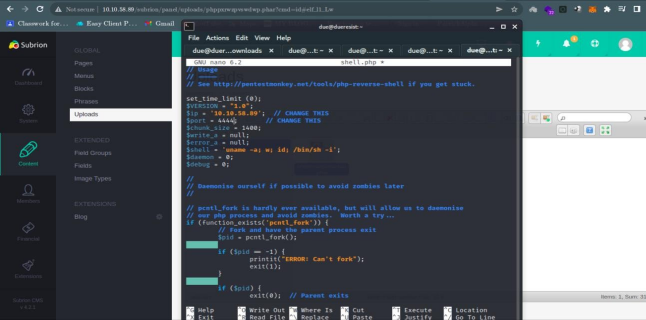
All I had to do was to change the IP to my tun0 and the listening port to the port of my wish then creating a netcat listener where a connection was established after uploading the php reverse shell and navigating to its link.

Now we have a proper tty(TeleTYpewriter) shell.
Now all we need to do is to stabilize the shell:
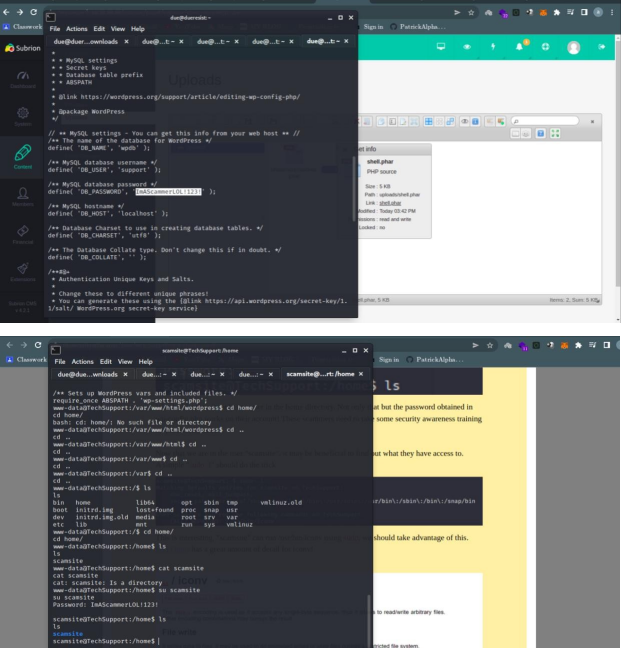
Bingo we have our flag; Running ‘sudo-l’ allows us to obtain commands that can be run as root by the current user and navigating to https://gtfobins.github.io/gtfobins/iconv/ I was able to view the Flag
